Edge Computing in Industrial IoT: Architectural Solutions for Mission-Critical Applications
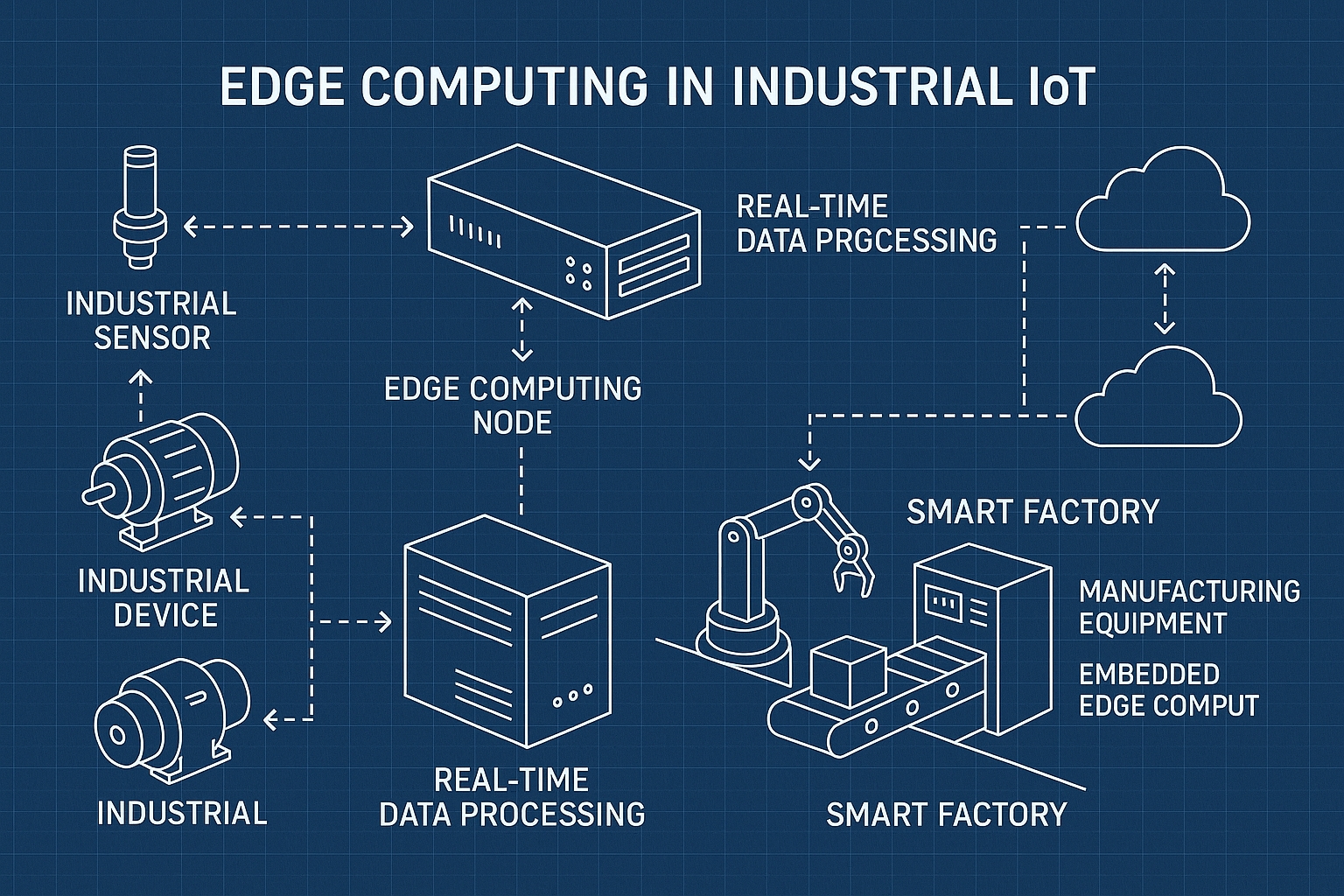
The transformation of industrial operations through edge computing represents a fundamental shift in how we approach distributed intelligence and real-time decision-making in manufacturing environments. As Industrial Internet of Things implementations mature beyond simple data collection paradigms, the demand for sophisticated edge computing architectures that can handle mission-critical applications with deterministic performance characteristics has become paramount. This comprehensive analysis explores the advanced architectural patterns, deployment strategies, and implementation frameworks that define the next generation of edge-enabled industrial systems.
The complexity of modern industrial environments demands computing architectures that transcend traditional centralized models. Edge computing in Industrial IoT contexts must simultaneously address latency constraints measured in microseconds, reliability requirements exceeding 99.999% availability, and security frameworks that protect against both cyber and physical threats. These requirements necessitate a fundamental rethinking of how computational resources are distributed, orchestrated, and managed across industrial networks.
Architectural Foundations of Industrial Edge Computing
The architectural foundations of edge computing in industrial environments extend far beyond simple distributed processing models to encompass sophisticated hierarchical structures that mirror the operational complexities of modern manufacturing systems. Contemporary industrial edge architectures must accommodate multiple layers of computational abstraction, from device-level embedded intelligence to plant-wide optimization algorithms, while maintaining strict deterministic behavior and fault tolerance characteristics.
At the foundational level, industrial edge computing architectures are characterized by their heterogeneous nature, incorporating diverse computational platforms ranging from microcontroller-based sensor nodes to high-performance computing clusters deployed at the plant floor level. This heterogeneity demands sophisticated abstraction layers that can present uniform programming models while accommodating the vastly different computational capabilities and constraints present across the edge continuum.
The temporal characteristics of industrial edge computing architectures represent a critical design dimension that distinguishes them from general-purpose edge computing implementations. Industrial processes operate within strict timing constraints where control loop delays measured in milliseconds can result in product quality degradation or safety incidents. Consequently, edge computing architectures must incorporate real-time operating systems, deterministic networking protocols, and predictable resource allocation mechanisms that can guarantee timing behavior under varying operational conditions.
Resource management in industrial edge environments requires sophisticated coordination mechanisms that can dynamically allocate computational resources based on changing process requirements while maintaining strict isolation between critical and non-critical applications. The concept of computational sovereignty becomes particularly relevant in industrial contexts, where edge nodes must be capable of autonomous operation during network partitions or upstream system failures, maintaining essential control functions and safety interlocks without external dependencies.
The integration of edge computing with existing industrial control systems presents unique architectural challenges that require careful consideration of both functional and non-functional requirements. Modern industrial facilities typically incorporate multiple generations of automation technology, from legacy Programmable Logic Controllers using proprietary communication protocols to modern Distributed Control Systems with standardized interfaces. Edge computing architectures must seamlessly integrate with these existing systems while providing migration paths toward more advanced computational paradigms.
Computational Paradigms and Processing Models
The computational paradigms employed in industrial edge computing environments represent a sophisticated evolution of traditional distributed computing models, incorporating domain-specific optimizations that address the unique requirements of industrial applications. These paradigms must simultaneously accommodate the high-frequency, low-latency demands of control applications with the complex analytical requirements of optimization and prediction algorithms.
Stream processing architectures form the cornerstone of industrial edge computing, enabling continuous analysis of sensor data streams with minimal buffering delays. Unlike traditional batch processing approaches, stream processing in industrial contexts must maintain state consistency across potentially millions of data points while providing deterministic processing guarantees. Advanced stream processing frameworks incorporate complex event processing capabilities that can identify patterns and anomalies in real-time data streams, triggering immediate responses to changing operational conditions.
The concept of computational tiering becomes essential in industrial edge architectures, where different types of processing are allocated to specific computational layers based on their timing requirements and resource constraints. Time-critical control functions are typically executed on dedicated real-time processing units with guaranteed execution times, while complex analytical algorithms may be distributed across higher-capacity edge compute nodes with more flexible timing constraints.
Hybrid processing models that combine traditional control theory with machine learning algorithms represent an emerging paradigm in industrial edge computing. These models enable adaptive control systems that can optimize their behavior based on historical performance data while maintaining the stability guarantees required for industrial processes. The integration of neural network inference engines with traditional control algorithms requires careful architectural consideration to ensure that machine learning enhancements do not compromise system reliability or introduce unpredictable behavior.
The implementation of federated learning approaches in industrial edge environments enables collaborative algorithm development across multiple facilities while maintaining data privacy and security requirements. Edge nodes can participate in distributed training processes that improve global model performance while keeping sensitive operational data localized. This approach requires sophisticated coordination mechanisms that can manage model synchronization and versioning across distributed edge deployments.
Event-driven architectures play a crucial role in industrial edge computing by enabling efficient resource utilization and responsive system behavior. Rather than continuously polling sensors or executing unnecessary computational cycles, event-driven systems can remain in low-power states until specific conditions trigger processing activities. This approach is particularly valuable in battery-powered edge deployments or environments with limited computational resources.
Mission-Critical Application Frameworks
Mission-critical applications in industrial edge computing environments demand specialized frameworks that can provide deterministic performance guarantees while maintaining the flexibility required for complex industrial processes. These frameworks must incorporate advanced fault tolerance mechanisms, real-time scheduling algorithms, and safety-critical design patterns that can ensure continuous operation even under adverse conditions.
Safety-critical control applications represent the most demanding class of industrial edge applications, requiring frameworks that can provide mathematically provable safety guarantees. These frameworks typically incorporate formal verification methodologies that can demonstrate compliance with safety standards such as IEC 61508 or ISO 26262. The implementation of safety-critical frameworks requires careful consideration of hardware architecture, software design patterns, and testing methodologies that can provide the evidence required for safety certification.
Predictive maintenance applications leverage edge computing capabilities to implement sophisticated condition monitoring and failure prediction algorithms directly at the asset level. These applications must continuously analyze vibration, temperature, and other sensor data to identify early indicators of equipment failure while minimizing false positive rates that could lead to unnecessary maintenance interventions. Advanced predictive maintenance frameworks incorporate digital twin technologies that can simulate equipment behavior under various operating conditions, enabling more accurate prediction of remaining useful life.
Quality control applications in industrial edge computing environments require real-time image processing and pattern recognition capabilities that can identify defects or anomalies in manufactured products. These applications must operate at production line speeds while maintaining high accuracy rates, often requiring specialized hardware acceleration through Graphics Processing Units or Field-Programmable Gate Arrays. The implementation of quality control frameworks requires careful consideration of lighting conditions, camera positioning, and image processing algorithms that can provide consistent results across varying environmental conditions.
Energy management applications leverage edge computing capabilities to optimize power consumption and utility costs across industrial facilities. These applications must continuously monitor energy usage patterns and adjust equipment operation to minimize costs while maintaining production requirements. Advanced energy management frameworks incorporate demand response capabilities that can automatically adjust facility operations based on utility pricing signals or grid stability requirements.
The integration of augmented reality and digital twin technologies in industrial edge computing environments enables new classes of mission-critical applications focused on operator assistance and remote maintenance. These applications require low-latency rendering capabilities and precise spatial tracking to provide useful information overlays without introducing safety hazards. The implementation of augmented reality frameworks requires coordination between edge computing nodes, wearable devices, and centralized data repositories to provide seamless user experiences.
Distributed Intelligence and Autonomous Decision-Making
The evolution toward distributed intelligence in industrial edge computing represents a fundamental shift from centralized control paradigms to autonomous decision-making systems that can operate independently while maintaining coordination with broader industrial networks. This transformation requires sophisticated algorithms that can make optimal decisions based on local information while considering global optimization objectives and operational constraints.
Autonomous control systems in industrial edge environments must incorporate machine learning algorithms that can adapt to changing process conditions while maintaining stability and safety requirements. These systems typically employ reinforcement learning approaches that can optimize control parameters based on historical performance data and current operating conditions. The implementation of autonomous control requires careful consideration of exploration versus exploitation trade-offs to ensure that learning activities do not compromise operational safety or efficiency.
Multi-agent systems provide a powerful framework for implementing distributed intelligence in industrial edge computing environments. Individual edge nodes can operate as autonomous agents that pursue local objectives while participating in collaborative decision-making processes that optimize global system performance. The coordination of multi-agent systems requires sophisticated communication protocols and consensus algorithms that can handle network partitions and varying communication latencies.
Swarm intelligence approaches enable the implementation of distributed optimization algorithms that can solve complex scheduling and resource allocation problems across multiple edge nodes. These approaches are particularly valuable in applications such as fleet management, where individual vehicles must make autonomous decisions while coordinating with other vehicles to optimize overall system performance. The implementation of swarm intelligence requires careful consideration of communication overhead and convergence properties to ensure efficient operation.
The concept of computational markets provides an innovative approach to resource allocation in distributed edge computing environments. Edge nodes can participate in virtual markets where computational resources are traded based on supply and demand dynamics. This approach enables efficient resource utilization while providing natural mechanisms for handling varying workload demands and node failures.
Federated decision-making frameworks enable coordination between autonomous edge nodes while maintaining data privacy and security requirements. These frameworks allow edge nodes to share decision-making insights without revealing sensitive operational data, enabling collaborative optimization while maintaining competitive advantages. The implementation of federated decision-making requires sophisticated cryptographic protocols and consensus mechanisms that can provide security guarantees while maintaining operational efficiency.
| Application Domain | Latency Requirements | Reliability Requirements | Processing Complexity |
| Safety Control | < 1 millisecond | 99.9999% | Low to Medium |
| Quality Inspection | < 100 milliseconds | 99.99% | High |
| Predictive Maintenance | < 1 second | 99.9% | Very High |
| Energy Optimization | < 10 seconds | 99% | Medium |
| Process Optimization | < 1 minute | 99.9% | Very High |
Advanced Networking and Communication Protocols
The networking infrastructure supporting industrial edge computing applications must accommodate diverse communication requirements ranging from high-frequency control data with microsecond timing constraints to bulk data transfers for machine learning model updates. Advanced networking protocols specifically designed for industrial environments incorporate time-sensitive networking capabilities that can provide deterministic latency guarantees while maintaining high throughput for background data transfers.
Time-Sensitive Networking protocols represent a critical enabling technology for industrial edge computing, providing the deterministic communication capabilities required for distributed control applications. These protocols incorporate traffic shaping mechanisms that can guarantee bandwidth allocation and latency bounds for critical data flows while providing best-effort delivery for non-critical traffic. The implementation of Time-Sensitive Networking requires careful network topology design and configuration to ensure that timing guarantees can be maintained across complex industrial networks.
Wireless communication technologies play an increasingly important role in industrial edge computing, enabling flexible deployment of edge nodes without the constraints of wired infrastructure. Advanced wireless protocols such as 5G New Radio and Wi-Fi 6 provide the low-latency, high-reliability communication capabilities required for industrial applications. The implementation of wireless industrial networks requires careful consideration of interference sources, coverage requirements, and mobility patterns to ensure consistent performance.
Software-Defined Networking approaches enable dynamic reconfiguration of industrial networks based on changing application requirements and operational conditions. Edge computing applications can request specific network resources and quality of service guarantees through standardized interfaces, enabling automatic network optimization without manual intervention. The implementation of Software-Defined Networking in industrial environments requires careful consideration of security implications and integration with existing network infrastructure.
Network slicing technologies provide a mechanism for creating virtual networks with specific performance characteristics tailored to different classes of industrial applications. Critical control applications can be allocated dedicated network slices with guaranteed performance characteristics, while background data transfers can utilize shared network resources. The implementation of network slicing requires sophisticated resource management algorithms that can dynamically allocate network resources based on changing application demands.
Edge-to-edge communication protocols enable direct data exchange between edge nodes without requiring centralized coordination. These protocols are particularly valuable in applications such as collaborative robotics, where multiple robots must coordinate their activities in real-time. The implementation of edge-to-edge communication requires careful consideration of discovery mechanisms, routing protocols, and security frameworks that can provide secure, efficient communication.
Security Architecture and Threat Mitigationё
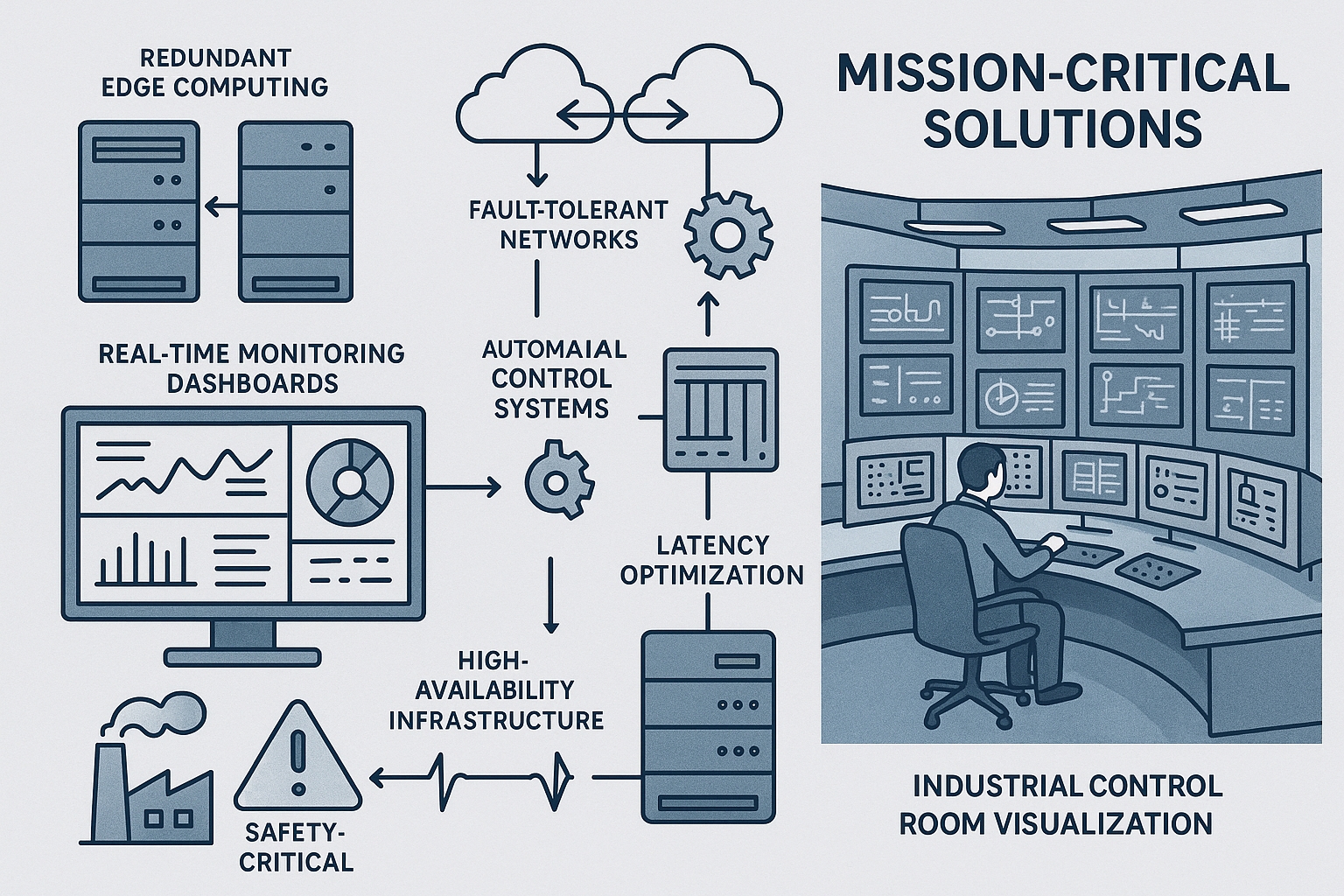
The security architecture for industrial edge computing environments must address unique threat vectors that arise from the combination of cyber and physical domains. Traditional cybersecurity approaches focused on network perimeter defense are insufficient for distributed edge computing environments where potentially compromised nodes must continue operating while maintaining system integrity.
Zero-trust architecture principles provide a comprehensive framework for securing industrial edge computing environments. Rather than assuming that devices within the network perimeter are trustworthy, zero-trust approaches require continuous authentication and authorization for all communication and resource access. The implementation of zero-trust architectures in industrial environments requires careful consideration of performance implications and integration with existing security infrastructure.
Hardware-based security technologies such as Trusted Platform Modules and Hardware Security Modules provide foundational security capabilities for industrial edge computing. These technologies can provide secure boot capabilities, encrypted storage, and cryptographic acceleration that enable sophisticated security protocols without significant performance overhead. The implementation of hardware-based security requires careful consideration of supply chain security and long-term key management requirements.
Intrusion detection and prevention systems specifically designed for industrial environments can identify and respond to both cyber attacks and physical security threats. These systems must incorporate domain-specific knowledge about industrial processes and equipment to distinguish between legitimate operational variations and malicious activities. Advanced intrusion detection systems can automatically isolate compromised edge nodes while maintaining essential industrial functions.
Blockchain and distributed ledger technologies provide innovative approaches to maintaining data integrity and audit trails in distributed edge computing environments. These technologies can provide immutable records of configuration changes, software updates, and operational events that can support forensic analysis and compliance requirements. The implementation of blockchain technologies in industrial environments requires careful consideration of performance implications and integration with existing data management systems.
Quantum-resistant cryptographic protocols are becoming increasingly important as quantum computing capabilities advance. Industrial edge computing systems with long operational lifespans must incorporate cryptographic algorithms that will remain secure against future quantum attacks. The implementation of quantum-resistant cryptography requires careful consideration of performance implications and migration strategies from existing cryptographic systems.
Performance Optimization and Resource Management
Performance optimization in industrial edge computing environments requires sophisticated algorithms that can balance competing objectives such as response time, energy consumption, and resource utilization while maintaining deterministic behavior. These optimization approaches must accommodate the highly variable and unpredictable nature of industrial workloads while providing consistent performance guarantees for critical applications.
Dynamic resource allocation algorithms enable edge computing systems to adapt to changing workload demands while maintaining performance guarantees for critical applications. These algorithms must consider multiple dimensions of resource constraints including computational capacity, memory availability, network bandwidth, and energy consumption. Advanced resource allocation approaches incorporate machine learning techniques that can predict future resource demands based on historical patterns and current operational conditions.
Load balancing strategies for industrial edge computing must accommodate the heterogeneous nature of edge nodes while maintaining data locality requirements and communication constraints. Unlike traditional load balancing approaches that focus primarily on computational load distribution, industrial edge computing requires consideration of real-time constraints, data dependencies, and safety requirements. Sophisticated load balancing algorithms can dynamically redistribute workloads based on node capabilities and current utilization while maintaining application performance requirements.
Caching and data management strategies play a crucial role in optimizing performance in industrial edge computing environments. Edge nodes must maintain local copies of frequently accessed data while implementing efficient synchronization mechanisms that can handle network partitions and varying communication latencies. Advanced caching strategies incorporate predictive algorithms that can prefetch data based on anticipated access patterns and operational schedules.
Energy optimization algorithms are particularly important in industrial edge computing deployments that operate on battery power or have limited energy budgets. These algorithms must balance computational performance with energy consumption while maintaining operational requirements. Advanced energy optimization approaches incorporate dynamic voltage and frequency scaling, workload scheduling, and sleep mode management that can minimize energy consumption without compromising application performance.
Real-time scheduling algorithms specifically designed for industrial edge computing must provide deterministic execution guarantees while maximizing system utilization. These algorithms must consider task priorities, deadline constraints, and resource requirements while handling dynamic workload changes and system failures. Advanced scheduling approaches incorporate machine learning techniques that can optimize scheduling decisions based on historical performance data and predicted future demands.
Digital Twin Integration and Simulation
The integration of digital twin technologies with industrial edge computing enables unprecedented levels of process optimization and predictive capabilities. Digital twins provide virtual representations of physical industrial assets that can be continuously updated with real-time data from edge sensors, enabling sophisticated simulation and analysis capabilities that would be impractical with traditional approaches.
Real-time digital twin implementations require sophisticated data synchronization mechanisms that can maintain consistency between physical assets and their virtual representations. Edge computing nodes must continuously stream sensor data to digital twin platforms while receiving control commands and configuration updates. The implementation of real-time digital twins requires careful consideration of data quality, synchronization delays, and computational requirements that can impact both physical and virtual system performance.
Predictive simulation capabilities enabled by digital twins allow industrial operators to evaluate the potential consequences of operational changes before implementing them in physical systems. Edge computing nodes can run simplified versions of digital twin models that provide immediate feedback on proposed changes while more complex simulations are performed on higher-capacity computing resources. This hybrid approach enables responsive decision-making while maintaining the accuracy of detailed simulation models.
Model-based control strategies leverage digital twin representations to implement advanced control algorithms that can optimize process performance beyond the capabilities of traditional control approaches. These strategies use digital twins to predict the behavior of physical systems under various control scenarios, enabling the selection of optimal control actions. The implementation of model-based control requires sophisticated model updating mechanisms that can maintain accuracy as physical systems age and operating conditions change.
Fault detection and diagnosis capabilities enhanced by digital twins can identify equipment problems before they result in operational failures. Edge computing nodes can continuously compare actual sensor readings with predicted values from digital twin models, identifying deviations that may indicate emerging problems. Advanced fault detection systems can automatically trigger maintenance activities or operational adjustments based on digital twin predictions.
The concept of digital twin orchestration enables coordination between multiple digital twin instances representing different aspects of complex industrial systems. Edge computing nodes can participate in distributed digital twin networks that provide comprehensive representations of entire industrial facilities. This approach enables system-level optimization and analysis that would be impossible with isolated digital twin implementations.
| Digital Twin Capability | Edge Computing Role | Performance Requirements |
| Real-time Data Synchronization | Sensor Data Collection | < 10ms latency |
| Predictive Simulation | Local Model Execution | < 100ms response |
| Fault Detection | Anomaly Detection | < 1s detection time |
| Control Optimization | Model-based Control | < 50ms control loop |
| System Orchestration | Distributed Coordination | < 1s coordination |
Scalability and Deployment Strategies
Scalability in industrial edge computing environments presents unique challenges that extend beyond traditional distributed computing scalability concerns. Industrial edge deployments must accommodate organic growth patterns, varying operational requirements, and equipment lifecycle considerations while maintaining consistent performance and reliability characteristics across the entire deployment.
Horizontal scaling strategies for industrial edge computing must consider the physical constraints and operational requirements of industrial environments. Unlike cloud computing environments where resources can be added dynamically, industrial edge scaling often requires careful planning and coordination with operational schedules. Advanced scaling strategies incorporate predictive capacity planning that can anticipate future resource requirements based on production forecasts and historical growth patterns.
Vertical scaling approaches enable individual edge nodes to accommodate increasing computational demands through hardware upgrades or software optimization. Industrial edge computing platforms must support seamless hardware upgrades that can be performed during scheduled maintenance windows without disrupting operational processes. The implementation of vertical scaling requires careful consideration of hardware compatibility, software migration strategies, and performance validation procedures.
Edge computing deployment strategies must accommodate the diverse operational requirements and physical constraints present in industrial environments. Greenfield deployments can leverage purpose-built edge computing infrastructure designed specifically for industrial applications, while brownfield deployments must integrate with existing industrial systems and infrastructure. Hybrid deployment strategies can combine purpose-built edge nodes with retrofitted existing equipment to provide comprehensive edge computing capabilities.
Containerization and virtualization technologies enable flexible deployment and management of edge computing applications across heterogeneous hardware platforms. Container orchestration platforms specifically designed for industrial environments can automatically deploy and manage edge applications while maintaining isolation and security requirements. The implementation of containerization in industrial environments requires careful consideration of real-time performance implications and resource overhead.
Automated deployment and configuration management systems enable efficient management of large-scale edge computing deployments. These systems can automatically provision new edge nodes, deploy applications, and manage configuration updates across distributed deployments. Advanced deployment management systems incorporate machine learning capabilities that can optimize deployment decisions based on historical performance data and operational requirements.
Future Technological Convergence
The convergence of multiple technological trends is reshaping the landscape of industrial edge computing, creating new possibilities for intelligent, autonomous industrial systems. Artificial intelligence acceleration at the edge, quantum computing capabilities, and advanced sensor technologies are combining to enable unprecedented levels of industrial automation and optimization.
Neuromorphic computing architectures represent an emerging paradigm that could revolutionize edge computing capabilities in industrial environments. These architectures mimic the structure and function of biological neural networks, providing extremely energy-efficient processing for pattern recognition and decision-making tasks. The implementation of neuromorphic computing in industrial edge environments could enable sophisticated artificial intelligence capabilities while maintaining the low power consumption required for battery-powered deployments.
Quantum sensing technologies are beginning to enable new classes of industrial measurement and monitoring applications that require edge computing capabilities. Quantum sensors can provide unprecedented accuracy for measuring magnetic fields, gravitational variations, and other physical phenomena that are important for industrial processes. The integration of quantum sensing with edge computing requires specialized algorithms and hardware architectures that can leverage quantum measurement capabilities.
Advanced materials and manufacturing technologies are enabling the development of edge computing devices specifically optimized for industrial environments. These devices can incorporate specialized sensors, actuators, and computing capabilities in ruggedized packages that can withstand harsh industrial conditions. The development of application-specific edge computing devices requires close collaboration between hardware designers, software developers, and industrial domain experts.
The convergence of edge computing with augmented reality and mixed reality technologies is creating new possibilities for human-machine interaction in industrial environments. Edge computing capabilities can provide real-time rendering and spatial tracking required for immersive augmented reality experiences while maintaining the low latency required for safety-critical applications. The implementation of augmented reality in industrial environments requires sophisticated edge computing architectures that can coordinate between wearable devices, edge nodes, and centralized systems.
Implementation Considerations and Best Practices
The successful implementation of industrial edge computing systems requires careful consideration of numerous technical, operational, and organizational factors that can impact both short-term deployment success and long-term operational sustainability. These considerations extend beyond traditional information technology concerns to encompass operational technology requirements, safety considerations, and regulatory compliance obligations.
Hardware selection for industrial edge computing deployments must balance computational capabilities with environmental requirements, power constraints, and long-term availability considerations. Industrial environments often present challenging conditions including extreme temperatures, vibration, electromagnetic interference, and exposure to chemicals or moisture. Hardware platforms must be specifically designed or qualified for these environments while providing the computational capabilities required for edge applications.
Software architecture decisions have profound implications for the long-term maintainability and scalability of industrial edge computing systems. Modular software architectures that separate application logic from hardware-specific implementations enable flexibility and portability across different edge computing platforms. The implementation of standardized interfaces and communication protocols facilitates integration with existing industrial systems and future technology upgrades.
Testing and validation strategies for industrial edge computing systems must address both functional and non-functional requirements while considering the safety-critical nature of many industrial applications. Comprehensive testing approaches must include functional testing, performance testing, security testing, and environmental testing that can provide confidence in system behavior under various operational conditions. The development of automated testing frameworks can reduce testing costs while improving test coverage and repeatability.
Change management and configuration control processes become particularly important in industrial edge computing environments where system changes can have significant operational and safety implications. Formal change management processes must balance the need for rapid deployment of updates and improvements with the requirements for thorough testing and validation. The implementation of automated configuration management systems can reduce the risk of configuration errors while maintaining audit trails for compliance purposes.
Training and skill development programs are essential for organizations implementing industrial edge computing systems. The convergence of information technology and operational technology requires personnel with interdisciplinary skills that span multiple technical domains. Effective training programs must address both technical skills and operational considerations while providing hands-on experience with actual industrial edge computing systems.
Economic Models and Return on Investment
The economic justification for industrial edge computing implementations requires sophisticated analysis that considers both direct cost savings and indirect benefits that may be difficult to quantify. Traditional return on investment calculations may not adequately capture the value of improved operational flexibility, reduced risk, and enhanced competitive capabilities that can result from edge computing deployments.
Cost-benefit analysis for industrial edge computing must consider both capital expenditures and operational expenditures while accounting for the extended operational lifespans typical of industrial equipment. Edge computing systems may require significant upfront investments in hardware, software, and implementation services, but these costs must be evaluated against potential savings from reduced downtime, improved efficiency, and enhanced product quality over the system’s operational lifetime.
Risk mitigation benefits represent a significant but often overlooked source of value from industrial edge computing implementations. Edge computing systems can reduce the risk of catastrophic failures, regulatory violations, and safety incidents that could result in substantial financial losses. The quantification of risk reduction benefits requires sophisticated modeling approaches that can estimate the probability and potential impact of various failure scenarios.
Competitive advantage considerations become increasingly important as industrial edge computing becomes more widespread. Organizations that successfully implement edge computing capabilities may gain significant advantages in operational efficiency, product quality, and customer responsiveness that can translate into increased market share and profitability. The evaluation of competitive advantage benefits requires careful analysis of market dynamics and competitive positioning.
Financing and procurement strategies for industrial edge computing must accommodate the unique characteristics of these systems while optimizing total cost of ownership. Leasing arrangements, managed service contracts, and performance-based contracting can provide alternative financing approaches that may be more attractive than traditional capital expenditure models. The selection of appropriate financing strategies requires careful consideration of tax implications, accounting requirements, and operational flexibility needs.
Regulatory Compliance and Standards
The regulatory landscape for industrial edge computing is complex and evolving, encompassing safety standards, cybersecurity requirements, data privacy regulations, and industry-specific compliance obligations. Organizations implementing edge computing systems must navigate this regulatory environment while maintaining operational efficiency and competitive advantage.
Functional safety standards such as IEC 61508 and industry-specific derivatives provide frameworks for ensuring that edge computing systems can operate safely in industrial environments. These standards specify requirements for system architecture, software development processes, and testing procedures that must be followed to achieve safety certification. The implementation of safety-compliant edge computing systems requires significant investment in design processes, documentation, and testing that can impact project timelines and costs.
Cybersecurity standards and regulations are becoming increasingly stringent as the potential impact of cyber attacks on industrial systems is better understood. Standards such as IEC 62443 provide comprehensive frameworks for implementing cybersecurity measures in industrial automation systems, including edge computing components. Compliance with cybersecurity standards requires ongoing investment in security measures, monitoring systems, and incident response capabilities.
Data privacy regulations such as the General Data Protection Regulation and similar laws in other jurisdictions have significant implications for industrial edge computing systems that collect and process personal data. These regulations specify requirements for data collection, processing, storage, and transfer that must be incorporated into edge computing system designs. The implementation of privacy-compliant edge computing systems requires careful consideration of data flows, consent mechanisms, and individual rights management.
Industry-specific regulations such as those governing pharmaceutical manufacturing, food processing, and chemical production may impose additional requirements on edge computing systems used in these environments. These regulations often specify requirements for data integrity, audit trails, and system validation that must be addressed in edge computing implementations. Compliance with industry-specific regulations requires deep understanding of regulatory requirements and close collaboration with regulatory affairs specialists.
The emergence of artificial intelligence and machine learning in industrial edge computing is creating new regulatory challenges that are not yet fully addressed by existing standards and regulations. Organizations implementing AI-enabled edge computing systems must anticipate future regulatory requirements while ensuring that their systems can be modified to accommodate new compliance obligations as they emerge.
Conclusion
The evolution of edge computing in Industrial IoT environments represents a fundamental transformation in how we approach distributed intelligence and autonomous decision-making in manufacturing and industrial contexts. The architectural solutions, implementation strategies, and technological approaches explored in this comprehensive analysis demonstrate the sophisticated capabilities required to successfully deploy edge computing systems that can meet the demanding requirements of mission-critical industrial applications.
The convergence of advanced computing technologies, artificial intelligence, and industrial domain expertise is creating unprecedented opportunities for operational optimization, predictive maintenance, and autonomous control systems. However, the successful implementation of these capabilities requires careful consideration of architectural design patterns, security frameworks, and operational requirements that are unique to industrial environments.
The technical complexity of industrial edge computing systems demands interdisciplinary expertise that spans multiple domains including computer science, control theory, industrial engineering, and cybersecurity. Organizations that can successfully integrate these diverse skill sets and technological capabilities will be positioned to realize significant competitive advantages through enhanced operational efficiency, improved product quality, and reduced operational risks.
The economic implications of industrial edge computing extend far beyond simple cost reduction to encompass new business models, competitive positioning, and market opportunities. The quantification of these benefits requires sophisticated analytical frameworks that can capture both direct and indirect value creation while accounting for the long-term operational characteristics of industrial systems.
As the regulatory landscape continues to evolve and new technological capabilities emerge, the industrial edge computing ecosystem will continue to mature and expand. The architectural foundations and implementation strategies established today will provide the foundation for the next generation of intelligent, autonomous industrial systems that will define the future of manufacturing and industrial operations.
The path forward requires continued investment in research and development, standards development, and workforce education to ensure that the full potential of industrial edge computing can be realized while maintaining the safety, security, and reliability requirements that are essential for industrial applications. The organizations and individuals that can successfully navigate this complex technological landscape will be the leaders in the next phase of industrial evolution.
 iiotsphere.com
iiotsphere.com